Durch meine Unsicherheit, verließen mich alle Frauen, die ich bisher erobern konnte. Eine Partnerin erzähle mir einmal, ihr Ex-Freund habe Einen 21 Zentimeter gehabt. Da wurde ich total wütend und traurig zugleich. Warum diese Ungerechtigkeit, Warum hatter ihr Ex einen größeren Penis? Ich hatte ein neues Ziel: endlich einen größeren Penis! Ich wollte mich keiner operativen Penisvergrößerung, da ich die mögliche Risiken einer OP fürchtete. Narkose, dann ein falscher Schnitt und aus 8,8 Zentimeter könnten quasi 0 Zentimeter werden und ich könnte keine Erektion mehr bekommen. Nein, das wollte ich einfach nicht. Also suchte ich einige Tage im Netz nach Alternativen.
Ich stieß auf eine Sortiment von Pillen, auf Cremes und auf billige Penispumpen und weiter Artikel mit vielen unzufrieden Kunden. Viele dieser Produkte versprachen 9 cm mehr in zwei Tagen, was natürlich unmöglich ist. Keine dieser Alternativen war für mich seriös und erfolgsversprechend genug, um sie zu bestellen oftmals wurden viele dieser Produkte zu einem unmenschlichen Preis verkauft. Nach weiterer Suchen und tausenden Webseiten stieß ich letztendlich auf den Phallosan Forte von der schweizer Frima Swiss Sana, deren wissenschaftliche Studie und freundlicher Service per E Mail mich sofort überzeugte. Die positive Erfahrung und Ergbnisse verschiedener Benutzer und Kunden mit Phallosan Forte wurde auch in diveresen Internet Foren bestätigt. Zudem ist Phallosan Forte auch bei Amazon (dort auch per Express- Versand erhätlich, allerdings mit höhren Versandkosten verbunden) und in jeder normalen Apotheke erhältlich . Das gab mir Sicherheit. Daher wandert dieser Artikel dirkt in meinen Warenkorb . Ich kaufte also mein Phallosan Forte Set zu dem besten Preis, nämlich direkt auf der Website vom Hersteller.
Anwendungsgebiete des Phallosans von Swiss Sana
Bei Phallosan forte handelt sich um einen Penisextender,welcher sich die Vakuum Technik zunutze macht und direkt auf den Penis des Anwenders wirkt – und zwar durch eine Dehnung. Diese Dehnung führt zu einer verstärkten Bildung von neuen Zellen im Bereich der Eichel, was zu einer Vergrößerung des Penis führt.
Das Phallosan Gurtsystem kann unsichtbar unter der Hose getragen werden, indem er auf dem Penis platziert und anschließend mit einem Gurt fixiert wird. Im Alltag hat man mit der Benutzung von diesem medizinischen Hilfsmittel daher keine Schwirigkeiten. Auch das Tragen des Phallosans in der Nacht ist nicht unangenhem. Die Anwendung schmerzfrei, ist bequem, unauffällig und bringt gute Ergebnisse bei den verschiedensten Herausforderungen rund um den Penis. Das Vakuum Protektor System kann zur Penisvergrößerung und Penisverlängerung sowie bei Erektionsstörung verwendet werden. Laut der Swiss Sana Anstalt kann ihre Gerät auch zut Prostata Op Nachsorge verwendet werden. Somit biete das Phallosan forte System einen rund um Serive und kann sich damit einen Namen als Alleskönner machen.
Phallosan forte für die Behandlung einer Penisverkrümmung
Für den Fall, dass ein Mann an einer Verkrümmung leidet, funktioniert Phallosan Forte ebenfalls und dient zur Penisbegradigung und nicht nur zu Penisverlängerung. Und zwar als orthopädisches Extensionsgerät. Binnen von kurzer Zeit – einigen Monaten – kann dises optische Markel behoben werden. Ein operativer Eingriff wird somit umgangen.
Neben einer medikamentösen Behandlung ist ansonsten bei einer Penisverkrümmung häufig auch eine Operation nötig, um die Fehlstellung zu korrigieren.
Phallosan forte für die Behandlung einer Erektilen Dysfunktion (Erektionsprobleme)
Dank der Verwendung vom Phallosan forte Gurtsystem wird deine bestes Stück besser durchblutet, daher ist dieser Extender eine gute Alternative zu anderen Potenzmitteln zur Behandlung von Erektionsstörungen genutz werden . Gerade bei Anwendern im höheren Altern, die neben einem zu kleinen Penis auch an einer Erektilen Dysfunktion leiden, hat die Anwendung von diesem Gerät den positiven Nebeneffekt, dass der Penis stärker durchblutet wird und die Erektilen Dysfunktion gelindert wird. Auch bei einer Prostata OP wir das Vakuum Protektor zur Nachsorge verwendet.
Verbesserung bei vorzeitigem Samenerguss
Nicht nur bei dem Wunsch nach einem größeren Penis wird der Phallosan verwendet. Auch bei einer weiteren Sexualstörung – dem vorzeitigen Samenerguss – kann die Anwendung von Phallosan forte helfen. Dieses Situation kennen nicht nur ältere Männer. Auch viele jüngere Männer leiden darunter. Wenn hier auch keine Medikamente helfen sollten, kann es auch hier früher oder später zu einem Termin im OP-Saal kommen.
Durch die Anwendung vom Phallosan forte System kann dies jedoch verhindert werden. Denn wie bei der Erektilen Dysfunktion wirkt dieses Gerät auch, weil der Penis dank der Anwendung von diesem Extender besser durchblutet wird. Denn eine schwache Durchblutung des Penis kann auch einen vorzeitigen Samenerguss bewirken.
Der Bestellvorgang des Penisverlängerungssystem
Ich wollte so wenig Aufmerksamkeit auf mein Problematik lenken, wie nur möglich. Mir war bewusst, dass ich das Phallosan Forte Gurtsystem (Einzelpreis 279 Euro) auch in allen Apotheken (dort aber teurer) erwerben könnte, was meiner Meinung nach sowieso schon für das Produkt spricht. Ich hatte vor den Blicken der Apotheker Angst, weshalb ich das Produkt in der Kombipackung direkt und sehr diskret beim Swiss Sana selbst bestellte. Der Bestellvorgang ist kinderlicht, mit nur einem Klick ist der Penisstrecker direkt im Warenkorb und wird dort (im Warenkorb) für 30 Minuten reserviert. Wie auf der Homepage versprochen wird, ist der Versand diskret. Auf der Verpackung steht nichts von Penisvergrößerung, Penisverlängerung, sondern nur dein Name. Das war für mich so wichitg, dass ich nochmal eine Anfrage per E Mail gestellt habe, um wirklich sicher zu gehen. Nur ein dezenter Firmenname, der nicht auf ein solches Produkt schließen lässt. Super! Und das Beste: Ich konnte auswählen ob ich mit PayPal, Kreditkarte (VISA & MasterCard) oder Überweisung (also Vorkasse) zahle!
Die Verpackung
Phallosan Forte wird deutschlandweit verschickt. Nach etwa drei Tagen erhielt ich meine Bestellung, per Standard- Versand, der Einzelpreis der Versandkosten ist vom Land des Empfängers abhäning. Es ist sehr klein und in weiß gehalten. Es sieht aus, als wären Bücher in der Verpackung gelagert bzw. verbinde ich diese mit einer kleinen Verpackungen. Wie ich oben bereits erwähnt hatte, steht nichts von Phallosan oder Penisvergrößerung drauf oder was auch nur irgendwie mit kleinem Penis zutun haben könnte. Der Absender ist sehr diskret. Die Verpackung ist relativ dünn, aber ausreichend. Im kleinen rechteckigen Phallosan Forte Karton ist das komplette Zubehör enthalten. Man muss also nichts dazukaufen, in der Kombipackung (Einzelpreis 279 Euro) ist alles drin was man braucht..
Inhalt der Phallosan Forte Box (S, M und L)
Der Artikel wird direkt von Swiss Sana, dem Hersteller verschickt. Jede Bestellung ist eine Kombipackung und enthält:
Der Inhalt ist folgender:
- ein elastischer Gurt zur Führung um die Taille
- eine Saugglocke, mit passendem Manschettenkondom in Größe L
- eine Saugglocke, mit passendem Manschettenkondom in Größe M
- eine Saugglocke, mit passendem Manschettenkondom in Größe S
- eine Zuggabel zur Regulation der stufenlosen Verstellbarkeit der Zugstärke (inklusive Adapter für den elastischen Tragegurt)
- eine Protektor-Kappe für die Eichel
- eine Saugpumpe
- Bedienungsanleitung und Dokumentationen (Als CD und als Büchlein)
- Eine Schablone zum Messen der Länge und Breite (zur Wahl der richtigen Saugglocke, diese gibt es in S, M und L)
Hier sieht man direkt: Jede Penisgröße wird unterstützt. Die Bedienungsanleitung der Kombipackung ist sehr detailliert geschrieben und enhält nützliche Hinweise sowie wie die eine oder andere Abbildung und dient als nützliche Hilfe. Auf der Seite des Herstellers können auch jederzeit Phallosan Forte Ersatzteile und Zubehör bestellt werden. Bei weiteren Fragen zur Kombipackung kann man sich per E mail auch an den Service des Herstellers wenden. Die meisten Antworten auf Fragen bezüglich der Forte Phallosan Kombipackung, dem Einzelpreis oder den Versandkosten bekommt man auch online auf der Website im FAQ.
Phallosan forte Studie
Phallosan forte macht eine natürliche Penisvergrößerung und Penisverlängerung möglich, dank des Vakuum Protektor System: Der Hersteller hat sich bei der Entwicklung seines Strecksystems durch die Naturvölker und deren Methoden, Körperteile zu vergrößern (z.B. den Hals), insipirieren lassen. Diese nutzen nämlich schon seit Jahrtausenden eine kontinuierliche Dehnung der Körperteile um die Bildung von neuen Zellen anzuregen und somit eine Vergrößerung zu erreichen.
Darüber hinaus flossen natürlich auch Erkenntnisse aus modernen wissenschaftlichen Verfahren in die Entwicklung von diesem medizinischen Hilfsmittel ein. Besondere Berücksichtigung fanden dabei die Forschungen in Bezug auf die Gewebeexpansion, welche durch eine konstante Dehnung zu Stande kommt.
Der Phallosan nutzt den eingesetzten Unterdruck und die Zugkraft, wodurch das dreidimensionale Wachstum (Verlängerung, Verbreiterung und Zunahme des Umfangs) des männlichen Geschelchtteils angeregt wird.
Viele Fragen, die ich per E Mail bekomme, handeln von der Studie zum Phallosan forte: Eine wissenschaftliche Studie durch Prof. Dr. Sohn vom Markuskrankenhaus in Frankfurt am Main stützt die Angaben des Herstellers seit 2005. Die Tabelle in diesem Artikel verweisst auf die Durchschnittsergebnisse von 100 Teilnehmern, welche das Phallosan Gurtsystem über einen Zeitraum von 6 Monaten getragen haben.
Im Jahre 2021 wird der Phallosan forte von vielen Urologen zur Penisbegradigung oder bei der Behandlung von Erektionsstörungen empfohlen, um die Risiken einer OP zur Penisvergrößerung und Penisverlängerung zu umgehen. Zusätzlich besitzt der Phallosan forte als einziges Gerät in diesem Bereich eine Pharmazentralnummer (PZN) und CE Zeichen.
Meine persönlichen Erfahrungen mit Phallosan Forte
Wie ich bereits erwähnt habe, habe ich diesen Artikel in der Kombipackung selber gekauft und getestet und konnte sichtliche Ergebnissenis mit diesem Penis- Extender erzielen. Diese Bewertung enthält dementsprechend meine persönlichen Erfahrungen und Bewertung des Phallosan Forte Gurtsystems. Ich kann also genau sagen was der Phallosan Forte mir im Test gebracht hat. Gerne verrate ich euch nun auch noch einige meiner Tipps zur Phallosan Forte Anwendung und zum Phallosan Forte vorher nachher Ergebnis.
Die einfache Anwendung
 Dank der Phallosan Forte Anleitung aus der Kombipackung und den übersichtlichen Inhaltsverzeichnis der Packungsbeilage, ist die Anwendung ist leichter als auf Demo Videos im Internet: Man beginnt damit, sein bestes Stück mit der Schablone zu messen. Ich sah, dass ich die Saugglocke in der Größe S benötigte.
Dank der Phallosan Forte Anleitung aus der Kombipackung und den übersichtlichen Inhaltsverzeichnis der Packungsbeilage, ist die Anwendung ist leichter als auf Demo Videos im Internet: Man beginnt damit, sein bestes Stück mit der Schablone zu messen. Ich sah, dass ich die Saugglocke in der Größe S benötigte.
Zunächst wird die Protektorkappe für die Eichel einfach übergestülpt. Das geht einfach und schnell und jeder sollte das hinbekommen. Nun beginnen wir mit der Saugglocke. Die Saugglocke ist mit einem kleinen Kondom ausgestattet. Es ist ähnlich wie ein normales Kondom, aber wesentlich dicker im Material. Man sollte beim Anlegen des Manschettenkondoms enorm aufpassen. Schließlich sollte dieses Kondom lange halten und während der gesamten Anwendung nicht kaputt gehen. Es darf nicht reißen und ich empfehle es langsam aufzurollen, ähnlich wie bei einem Luftballon. Also stülpt man es sich über die Eichel, was absolut keine Herausforderung ist und mit ein wenig Übung auch in kurzer Zeit erledigt. Wenn Ihr das so macht, reduziert ich die Chance darauf das dass Kondom reißt oder sich verformt. Die Saugglocke ist also auf der Eichel und das Manschettenkondom über der Protektorkappe angebracht und abgerollt.
Das fühlt sich zunächst irgendwie komisch an sowie eingepackt, aber ist keineswegs unangenehm. Oberhalb der Saugglocke befindet sich die Zuggabel von Phallosan Forte. Diese dient als Zwischenstück zwischen dem Glied (und der Saugglocke) und dem Tragegurt. Auf der Saugglocke befindet sich eine kleine Pumpe. Hier muss man einfacherweise nur wenig pumpen, um einen Vakuum in der Saugglocke entstehen zu lassen. Zischen zwei und vier Pumpstößen reichen hierfür. Danach wird das kleine Ventil verriegelt, um den Druck zu halten. Anschließend wird der weiche und elastische Tragegurt befestigt. Der große Ring wird über den Penis an das untere Ende geschoben und der Gurt um die Hüfte herum gelegt. Am anderen Ende wird dieser mit der Oberseite der Saugglocke, an der ja die Zuggabel angebracht ist, verriegelt. So liegt er immer seitlich bei Anwendung.
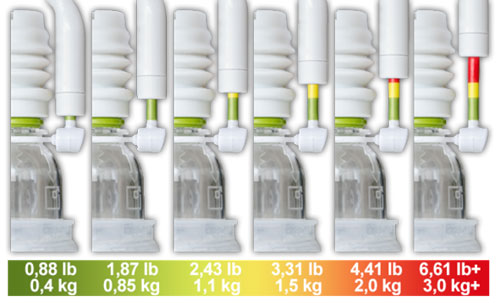
Mit der Zuggabel kann man dann nun die Zugkraft verstellen. Zwischen 0,4 Kilogramm und 3,0 Kilogramm kann man nun die Stärke variieren. Es ist in Ampelfarben gehalten und zeigt bei 0,4 Kilogramm die grüne Farbe an. Die Zugstärke kann also jeden Tag, je nach Belieben, verstellt werden. Oft denkt man, dass viel auch viel hilft, jedoch greift dies bei Phallosan Forte nur bedingt. Es wird empfohlen alle zwei Tage die Zugstärke zu regulieren. Man kann den Gurt bis zu 12 Stunden am Tag (oder auch in der Nacht) ohne Unanhemlichkeiten tragen. Es werden jedoch 6-8 Stunden täglich empfohlen. Insgesamt lässt sich der Phallosan Forte also einfach und schmerzfrei anlegen.
Komfort? Gibt es das bei Phallosan Forte?
Es mag auf den ersten Blick nicht so aussehen, aber das Tragen von Phallosan ist absolut komfortabel! Es stellt kein Hinderniss während eines 8 bis 10 Stunden langen Arbeitstages dar! Ich benutze Phallosan Forte aber überwiegend in der Nacht, was für mich einfach komfortabler ist, da man für den Toilettengang die Saugglocke und das Protektorkondom abnehmen muss. Mein Glied wächst also quasi im Schlaf, ohne dass ich beim Phallosan Forte Nebenwirkungen feststellen konnte.
Schlafen mit Phallosan Forte
Zunächst ist das Liegen auf dem Bauch gewöhnungsbedürftig, aber dennoch kein Dilemma. In der dritten Nacht hat es mich gar nicht mehr gestört. Ich trage beim Schlafen dazu ganz normale Boxershorts über dem Gurt mit Phallosan. Mit Slips könnte es jedoch unbehaglich werden. Deshalb empfehle ich ganz klar normale Shorts. Ebenfalls empfehle ich eine leichte Intimrasur, wodurch keine Haare abgerissen werden können. Dies ist mir auch nur ein einziges Mal passiert.
Der Alltag mit Phallosan Forte
Viele fragen sich sicherlich, ob man Phallosan Forte auch im normalen Arbeitsalltag tragen kann. Man sieht den Gurt von Phallosan Forte nicht von außen. Keine Dellen oder Beulen in der Hose. Auch Anzugshosen sind kein Herausforderung. Nur eine Sache ist enorm nervig: der Toilettengang. Jedes mal aus und anziehen. Deshalb empfehle ich Phallosan Forte einfach nachts zu tragen, danit er seine Dienste erfüllen kann!
Phallosan-App
Auch vor medizinischen Hilfsmitteln wie dem Forte Phallosan macht die Digitalisierung nicht halt. Der Hersteller, die Swiss Sana Anstalt von diesem Produkt ging daher voll mit der Zeit und hat eine App fürs Smartphone entwickelt. Sinn und Zweck der Verwendung von dieser App ist vor allem, dass die Erfolge und Ergebnisse der Penisvergrößerung beobachtet werden können. Die App ist sehr einfach aufgebaut und im Google Playstore für iOS und für Android erhältlich.
Meine abschließende Meinung und meine Ergebnisse:
Wie am Anfang bereits erwähnt habe kann man keine Verbesserungen innerhalb von zwei Tagen erwarten und auch keinen 9 cm Zuwachs. Ich konnte nach etwa 12 wöchigen Einsatz merken, dass der Penis sich ein Stück verlängert hatte. Das war etwas unter einem Zentimeter. Geschätzt würde ich sagen, das er um etwa 2,7 Zentimeter gewachsen ist. Ich war wirklich überschrasched von meinem Ergbnis und ich hätte nie, dass ich eine so gut Erfahrung und mit diesem Artikel haben werde. Leider hatte ich bei der ersten Messung, vor der Anwendung von Phallosan Forte, kein genaues Maßband zur Hand gehabt. Ich habe in einem weiteren Phallosan Forte Erfahrungsbericht im Internet gelesen, das einer der Kunden etwa 4,3 Zentimeter in sechs Monaten erreicht hat. Ich denke, dass ich ein kleines bisschen weniger erreichen konnte, aber bin fest überzeugt, dass Ergebnisse von bis zu 4 cm in sechs Monaten möglich sind.
Bei länger Nutzug von mindestens 12 Stunden am Tag vielleicht auch 5 cm. Dafür muss man Phallosan Forte natürlich konsequent anwenden und den Gurt tragen. Ich, als Single Mann, habe damit keinerlei Probleme. Jedoch sollte man nicht erwarten, dass man innerhalb von wenigen Tagen einen Erfolg von 5 cm verzeichnet. Das wäre absolut nicht realistisch und wird auch so vom Hersteller von Phallosan Forte nicht versprochen. Aber ein langsamer Fortschritt ist erkennbar und bei konsequenter Benutzung kann das Phallosan Forte Gurtsystem langfristige Erfolge garantieren.
Ich empfehle Männern mit einem kleinen Penis zur Anwendung von Phallosan Forte. Ich kann jedoch kein Urteil über eine Verdickung fällen, da ich glücklicherweise damit kein Problem. Nur die Länge ist alles andere als optimal. Ich kann jedoch sagen das Phallosan Forte funktioniert. Ich kann jedem Mann der über einer Penisvergrößerung, Penisverlängerung nachdenkt, oder an jenen die Erektionsprobleme haben dieses Produkt der Swiss Sana Anstalt nur empfehlen. Ich bin von diesem Artikel in allen Bereichen überzeugt, insbesondere durch den unschlagbaren Preis, schnellen Versand und geringern Versandkosten. Der freundliche Service gibt Antwortauf alle Fragen (per E Mail oder auch telefonisch). Ich würde dem Forte Phallsoan jedezeit wieder eine super Bewertung geben und kann ihn uneingeschränkt weiterempfehlen!